

HOTSPOT
-
You have a Microsoft 365 subscription that contains the users shown in the following table.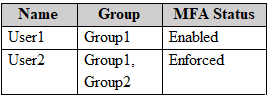
You have the named locations shown in the following table.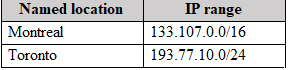
You create a conditional access policy that has the following configurations:
• Users or workload identities:
• Include: Group1
• Exclude: Group2
• Cloud apps or actions: Include all cloud apps
• Conditions:
• Include: Any location
• Exclude: Montreal
• Access control: Grant access, Require multi-factor authentication
User1 is on the multi-factor authentication (MFA) blocked users list.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.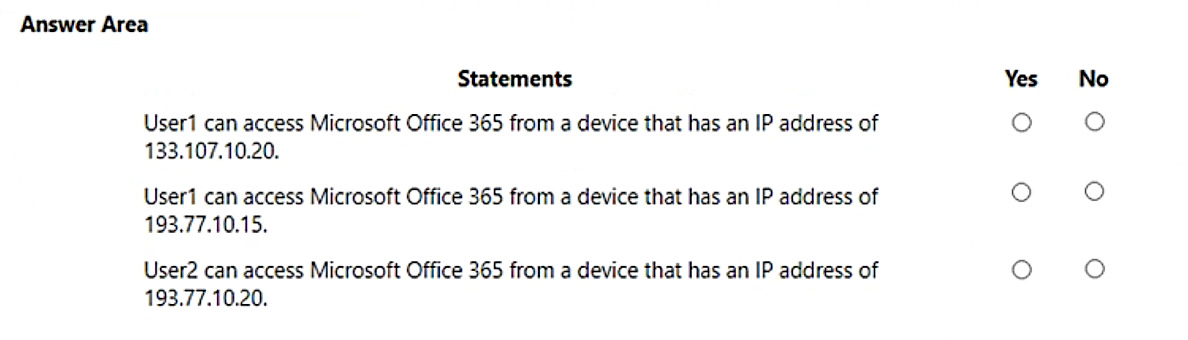
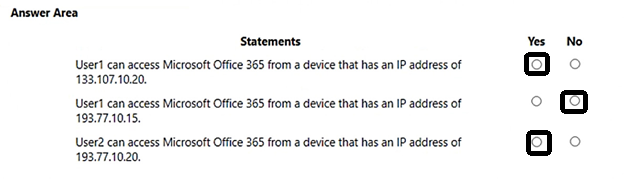
Correct Answer:
HOTSPOT
-
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.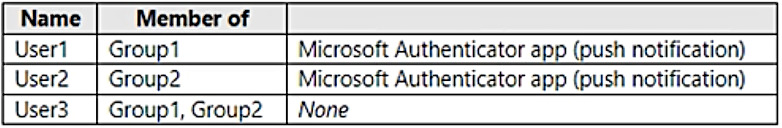
Each user has an Android device with the Microsoft Authenticator app installed and has set up phone sign-in.
The subscription has the following Conditional Access policy:
• Name: Policy1
• Assignments
• Users and groups: Group1, Group2
• Cloud apps or actions: All cloud apps
• Access controls
• Grant: Require multi-factor authentication
• Enable policy: On
From Microsoft Authenticator settings for the subscription, the Enable and Target settings are configured as shown in the exhibit. (Click the Exhibit tab.)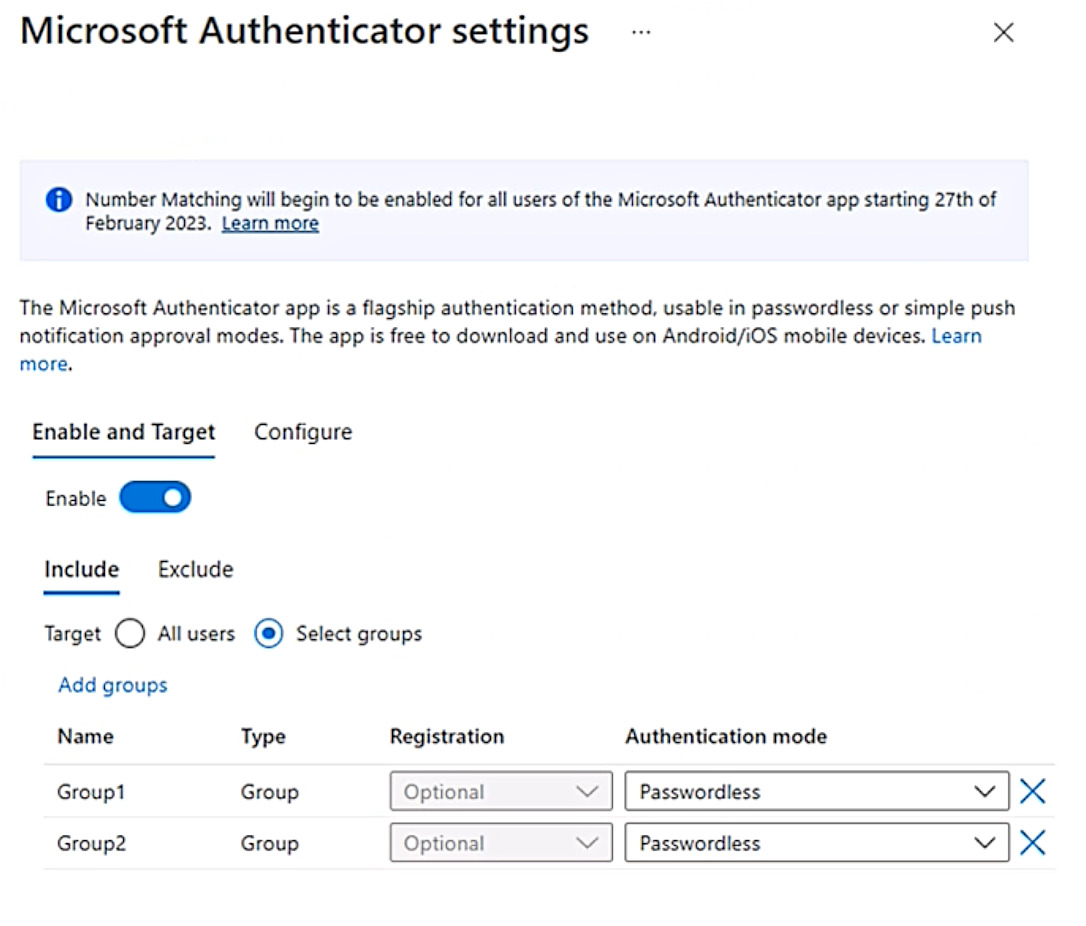
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.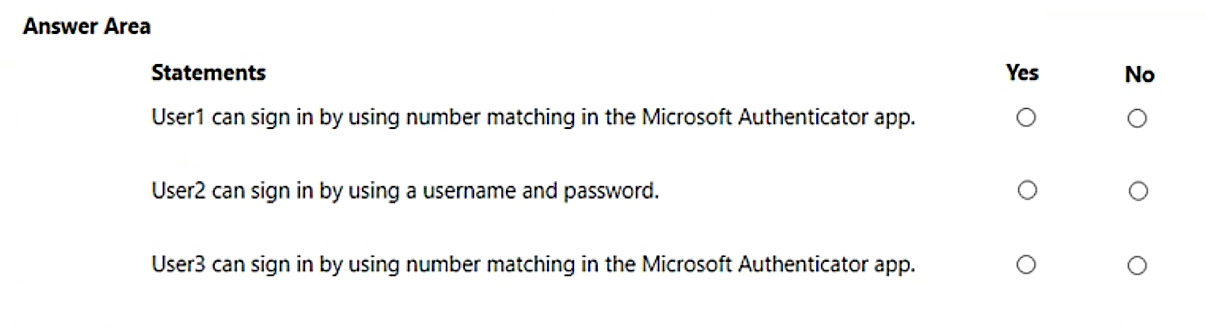
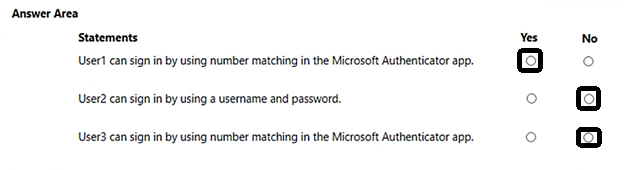
Correct Answer:
HOTSPOT
-
You have a Microsoft 365 subscription that uses an Azure AD tenant named contoso.com. The tenant contains the users shown in the following table.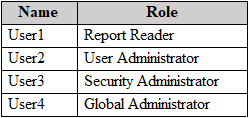
From the Sign-ins blade of the Microsoft Entra admin center, for which users can User1 and User2 view the sign-ins? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.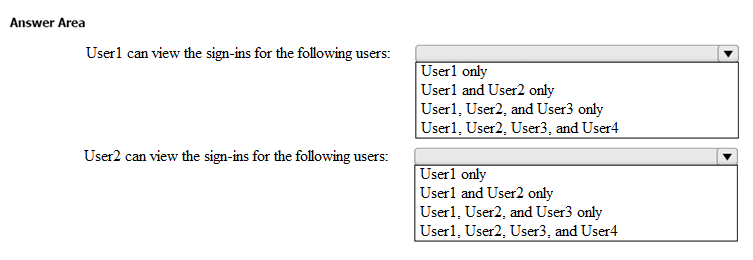
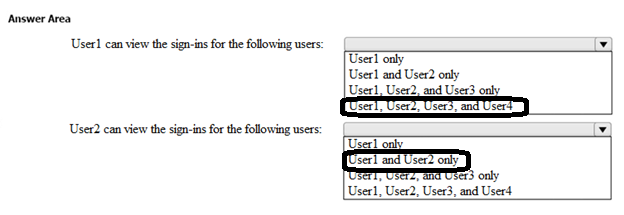
Correct Answer:
You have a Microsoft 365 subscription that contains an Azure AD tenant named contoso.com.
Corporate policy states that user passwords must not include the word Contoso.
What should you do to implement the corporate policy?
Correct Answer:
B
🗳️
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements:
• Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
• User passwords must be 10 characters or more.
Solution: Implement pass-through authentication and modify the password settings from the Default Domain Policy in Active Directory.
Does this meet the goal?
Correct Answer:
B
🗳️
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements:
• Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
• User passwords must be 10 characters or more.
Solution: Implement password hash synchronization and configure password protection in the Azure AD tenant.
Does this meet the goal?
Correct Answer:
B
🗳️
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements:
• Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
• User passwords must be 10 characters or more.
Solution: Implement pass-through authentication and configure password protection in the Azure AD tenant.
Does this meet the goal?
Correct Answer:
B
🗳️
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your network contains an Active Directory forest.
You deploy Microsoft 365.
You plan to implement directory synchronization.
You need to recommend a security solution for the synchronized identities. The solution must meet the following requirements:
• Users must be able to authenticate successfully to Microsoft 365 services if Active Directory becomes unavailable.
• User passwords must be 10 characters or more.
Solution: Implement password hash synchronization and modify the password settings from the Default Domain Policy in Active Directory.
Does this meet the goal?
Correct Answer:
A
🗳️
You have a Microsoft 365 E5 subscription. The subscription contains users that have the following types of devices:
• Windows 11
• Android
• iOS
To which devices can you apply Endpoint DLP policies?
Correct Answer:
A
🗳️
Your company has three main offices and one branch office. The branch office is used for research.
The company plans to implement a Microsoft 365 tenant and to deploy multi-factor authentication.
You need to recommend a Microsoft 365 solution to ensure that multi-factor authentication is enforced only for users in the branch office.
What should you include in the recommendation?
Correct Answer:
D
🗳️