

Note: This section contains one or more sets of questions with the same scenario and problem. Each question presents a unique solution to the problem. You must determine whether the solution meets the stated goals. More than one solution in the set might solve the problem. It is also possible that none of the solutions in the set solve the problem.
After you answer a question in this section, you will NOT be able to return. As a result, these questions do not appear on the Review Screen.
You have a Microsoft 365 E5 subscription.
You integrate Microsoft Defender for Endpoint with Microsoft Intune.
You need to ensure that devices automatically onboard to Defender for Endpoint when they are enrolled in Intune.
Solution: You create a compliance policy.
Does this meet the goal?
Correct Answer:
B
🗳️
HOTSPOT
-
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.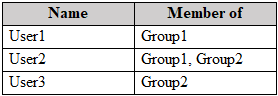
The subscription has the following two anti-spam policies:
• Name: AntiSpam1
• Priority: 0
• Include these users, groups and domains
• Users: User3
• Groups: Group1
• Exclude these users, groups and domains
• Groups: Group2
• Message limits
• Set a daily message limit: 100
• Name: AntiSpam2
• Priority: 1
• Include these users, groups and domains
• Users: User1
• Groups: Group2
• Exclude these users, groups and domains
• Users: User3
• Message limits
• Set a daily message limit: 50
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Correct Answer:
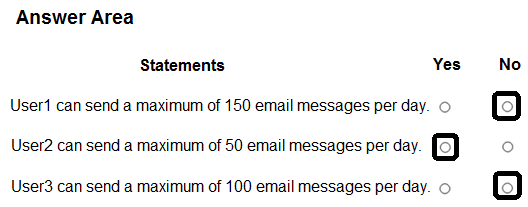
HOTSPOT
-
You have a Microsoft 365 E5 subscription that contains a user named User1 and the administrators shown in the following table.
User1 reports that after sending 1,000 email messages in the morning, the user is blocked from sending additional emails.
You need to identify the following:
• What administrators can unblock User1
• What to configure to allow User1 to send at least 2,000 emails per day without being blocked
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct Answer:

Overview -
Fabrikam, Inc. is an electronics company that produces consumer products. Fabrikam has 10,000 employees worldwide.
Fabrikam has a main office in London and branch offices in major cities in Europe, Asia, and the United States.
Existing Environment -
Active Directory Environment -
The network contains an Active Directory forest named fabrikam.com. The forest contains all the identities used for user and computer authentication. Each department is represented by a top-level organizational unit (OU) that contains several child OUs for user accounts and computer accounts.
All users authenticate to on-premises applications by signing in to their device by using a UPN format of username@fabrikam.com.
Fabrikam does NOT plan to implement identity federation.
Network Infrastructure -
Each office has a high-speed connection to the Internet.
Each office contains two domain controllers. All domain controllers are configured as DNS servers.
The public zone for fabrikam.com is managed by an external DNS server.
All users connect to an on-premises Microsoft Exchange Server 2016 organization. The users access their email by using Outlook Anywhere, Outlook on the web, or the Microsoft Outlook app for iOS. All the Exchange servers have the latest cumulative updates installed.
All shared company documents are stored on a Microsoft SharePoint Server farm.
Requirements -
Planned Changes -
Fabrikam plans to implement a Microsoft 365 Enterprise subscription and move all email and shared documents to the subscription.
Fabrikam plans to implement two pilot projects:
• Project1: During Project1, the mailboxes of 100 users in the sales department will be moved to Microsoft 365.
• Project2: After the successful completion of Project1, Microsoft Teams will be enabled in Microsoft 365 for the sales department users.
Fabrikam plans to create a group named UserLicenses that will manage the allocation of all Microsoft 365 bulk licenses.
Technical Requirements -
Fabrikam identifies the following technical requirements:
• All users must be able to exchange email messages successfully during Project1 by using their current email address.
• Users must be able to authenticate to cloud services if Active Directory becomes unavailable.
• A user named User1 must be able to view all DLP reports from the Microsoft Purview compliance portal.
• Microsoft 365 Apps for enterprise applications must be installed from a network share only.
• Disruptions to email access must be minimized.
Application Requirements -
Fabrikam identifies the following application requirements:
• An on-premises web application named App1 must allow users to complete their expense reports online. App1 must be available to users from the My Apps portal.
• The installation of feature updates for Microsoft 365 Apps for enterprise must be minimized.
Security Requirements -
Fabrikam identifies the following security requirements:
• After the planned migration to Microsoft 365, all users must continue to authenticate to their mailbox and to SharePoint sites by using their UPN.
• The membership of the UserLicenses group must be validated monthly. Unused user accounts must be removed from the group automatically.
• After the planned migration to Microsoft 365, all users must be signed in to on-premises and cloud-based applications automatically.
• The principle of least privilege must be used.
You are evaluating the required processes for Project1.
You need to recommend which DNS record must be created while adding a domain name to the tenant for the project.
Which DNS record should you recommend?
Correct Answer:
D
🗳️
HOTSPOT
-
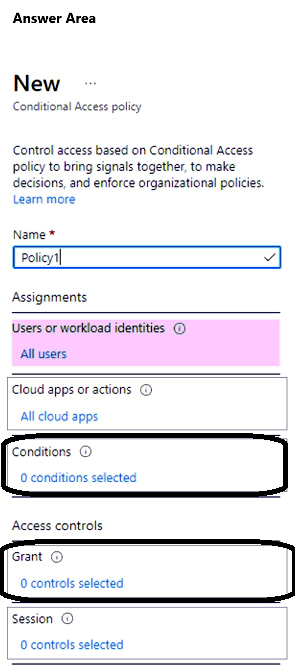
You have a Microsoft 365 E5 subscription.
You create a Conditional Access policy named Policy1 and assign Policy1 to all users.
You need to configure Policy1 to enforce multi-factor authentication (MFA) if the user risk level is high.
Which two settings should you configure in Policy1? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
Correct Answer:
Your network contains an Active Directory domain.
You have an Azure AD tenant that has Security defaults disabled.
Azure AD Connect is configured for directory synchronization. Password hash synchronization and pass-through authentication are disabled.
You need to enable Azure AD Identity Protection to detect leaked credentials.
What should you do first?
Correct Answer:
A
🗳️
HOTSPOT -
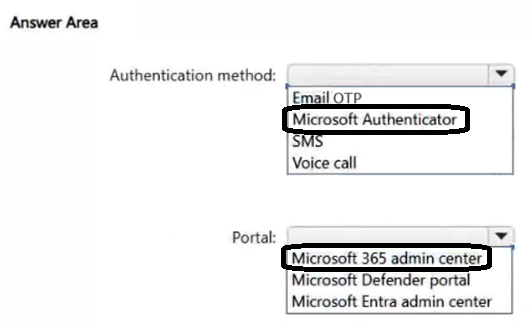
You have a Microsoft 365 E5 subscription.
You need to enable passwordless authentication for all users.
Which authentication method and portal should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct Answer:
Your network contains an on-premises Active Directory domain.
You have a Microsoft 365 subscription.
You implement a directory synchronization solution that uses pass-through authentication.
You configure Azure AD smart lockout as shown in the following exhibit.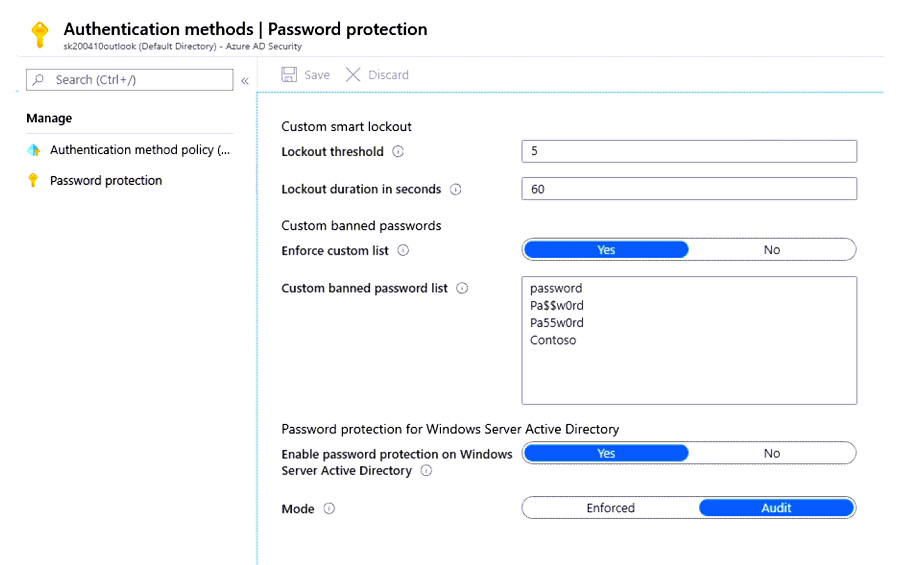
You discover that Active Directory users can use the passwords in the custom banned passwords list.
You need to ensure that banned passwords are banned for all users.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Correct Answer:
ADE
🗳️
Your network contains an Active Directory domain and an Azure AD tenant.
The network uses a firewall that contains a list of allowed outbound domains.
You begin to implement directory synchronization.
You discover that the firewall configuration contains only the following domain names in the list of allowed domains:
• *.microsoft.com
• *.office.com
Directory synchronization fails.
You need to ensure that directory synchronization completes successfully.
What is the best approach to achieve the goal? More than one answer choice may achieve the goal. Select the BEST answer.
Correct Answer:
A
🗳️
You have a Microsoft 365 E5 subscription that contains users in the United States, Europe, and Asia.
You use Azure AD Identity Protection.
You have a virtual desktop infrastructure (VDI). All VDI servers are located in the United States.
Users connect to Microsoft 365 from laptops and the VDI.
Some VDI users report that they are blocked from signing in to Microsoft 365 due to a high sign-in risk.
You need to reduce the likelihood that the VDI users will be erroneously blocked from signing in to Microsoft 365. The solution must ensure that sign-ins from the VDI environment are protected by using Identity Protection.
What should you configure?
Correct Answer:
B
🗳️