

You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint.
When users attempt to access the portal of a partner company, they receive the message shown in the following exhibit.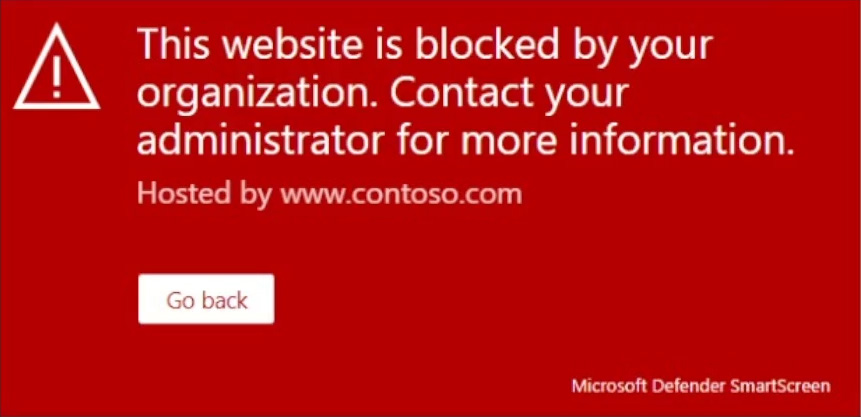
You need to enable user access to the partner company's portal.
Which Microsoft Defender for Endpoint setting should you modify?
Correct Answer:
E
🗳️
HOTSPOT -
You have a Microsoft 365 E3 subscription.
You plan to launch Attack simulation training for all users.
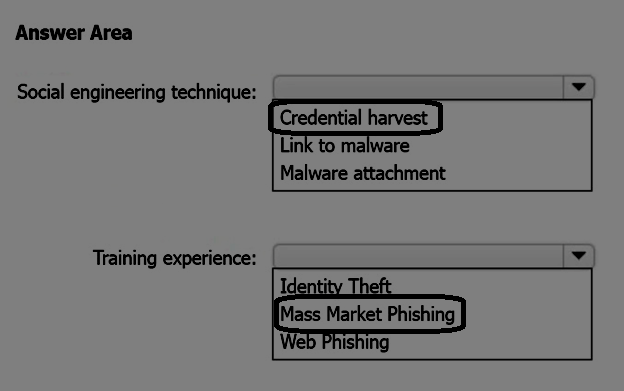
Which social engineering technique and training experience will be available? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Correct Answer:
You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365.
You need to ensure that users are prevented from opening or downloading malicious files from Microsoft Teams, OneDrive, or SharePoint Online.
What should you do?
Correct Answer:
D
🗳️
HOTSPOT -
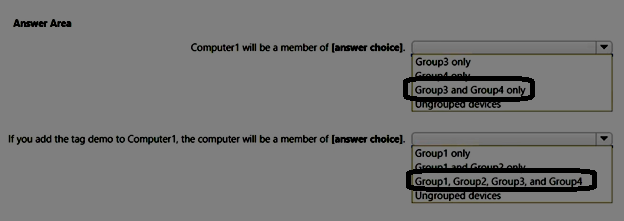
Your company uses Microsoft Defender for Endpoint. Microsoft Defender for Endpoint includes the device groups shown in the following table.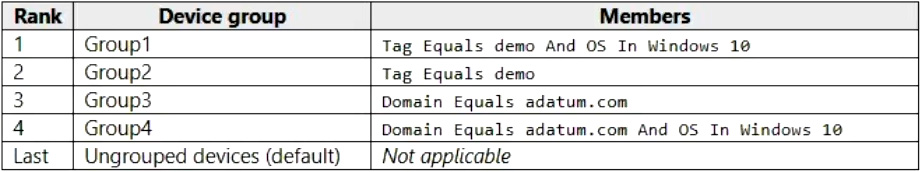
You onboard a computer named computer1 to Microsoft Defender for Endpoint as shown in the following exhibit.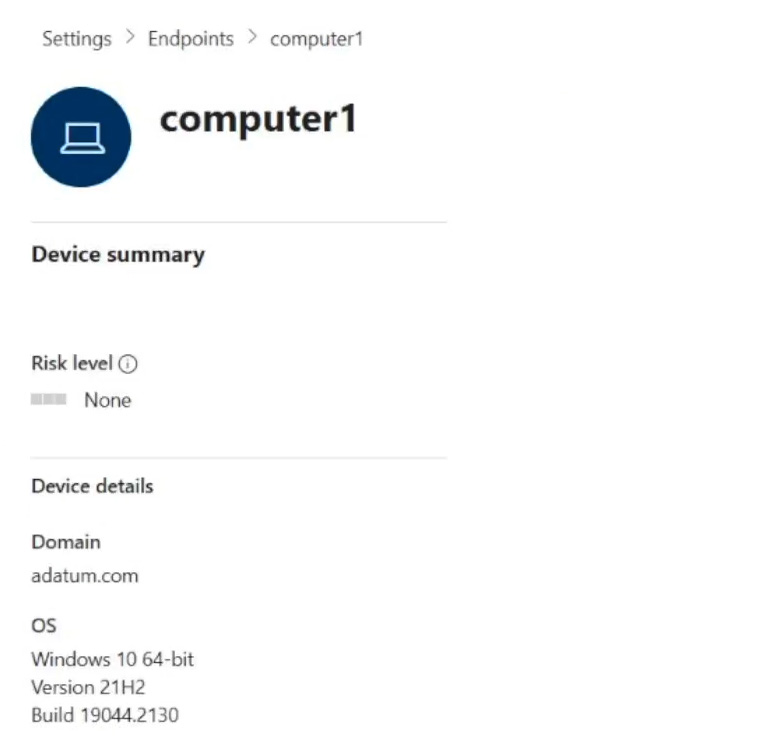
Use the drop-down menus to select the answer choice that completes each statement.
NOTE: Each correct selection is worth one point.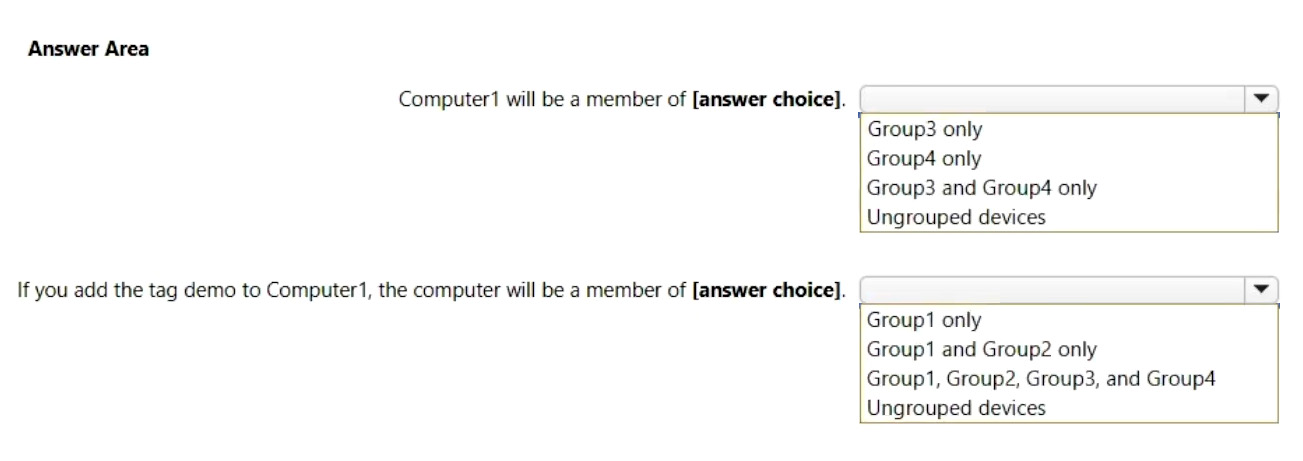
Correct Answer:
HOTSPOT -
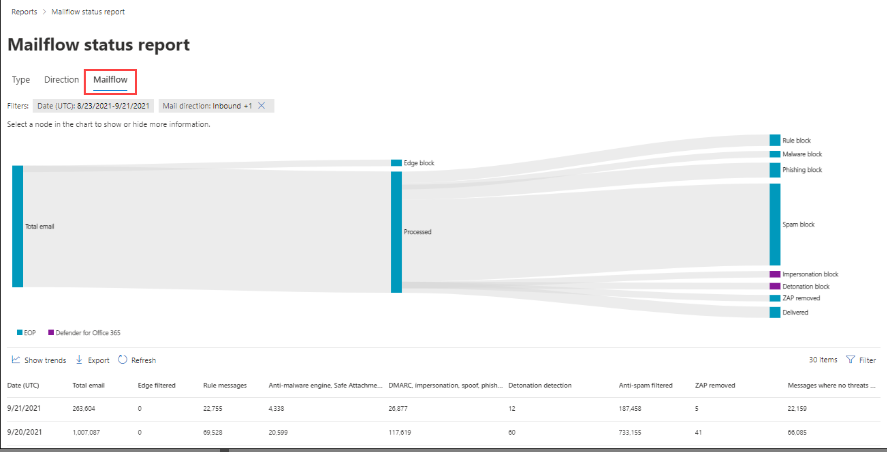
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Office 365.
The subscription has the default inbound anti-spam policy and a custom Safe Attachments policy.
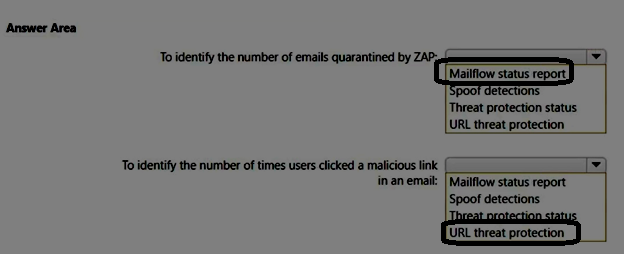
You need to identify the following information:
The number of email messages quarantined by zero-hour auto purge (ZAP)
The number of times users clicked a malicious link in an email message
Which Email & collaboration report should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.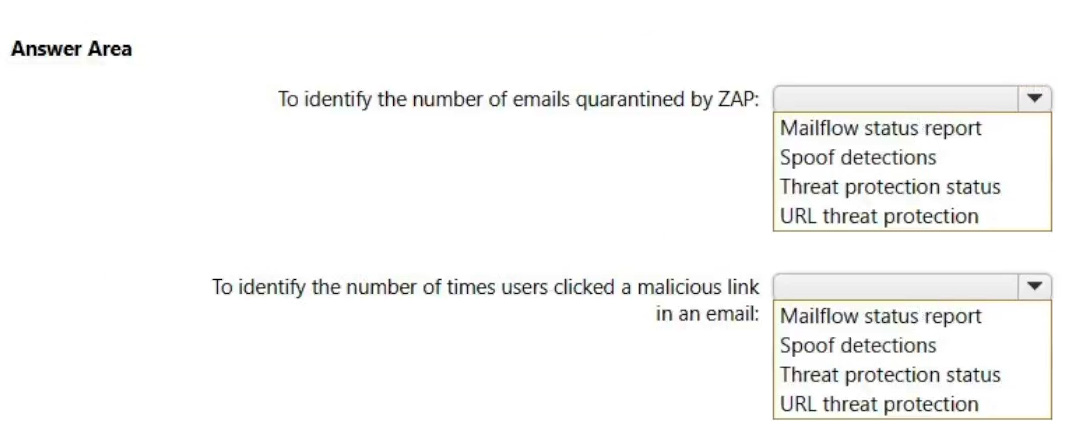
Correct Answer:
You have a Microsoft 365 tenant.
You plan to manage incidents in the tenant by using the Microsoft 365 Defender.
Which Microsoft service source will appear on the Incidents page of the Microsoft 365 Defender portal?
Correct Answer:
D
🗳️
Your network contains an on-premises Active Directory domain named contoso.local. The domain contains five domain controllers.
Your company purchases Microsoft 365 and creates an Azure AD tenant named contoso.onmicrosoft.com.
You plan to install Azure AD Connect on a member server and implement pass-through authentication.
You need to prepare the environment for the planned implementation of pass-through authentication.
Which three actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
Correct Answer:
CEF
🗳️
HOTSPOT -
You have a new Microsoft 365 E5 tenant.
Enable Security defaults is set to Yes.
A user signs in to the tenant for the first time.
Which multi-factor authentication (MFA) method can the user use, and how many days does the user have to register for MFA? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.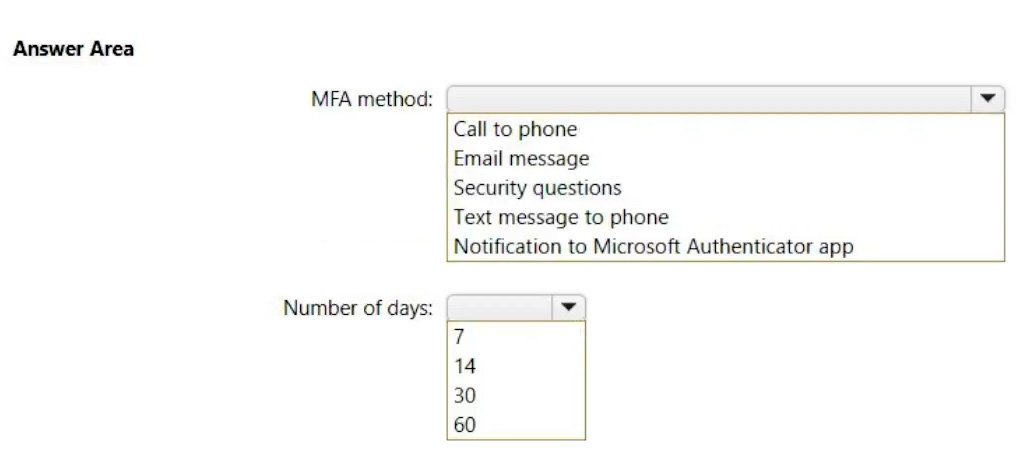
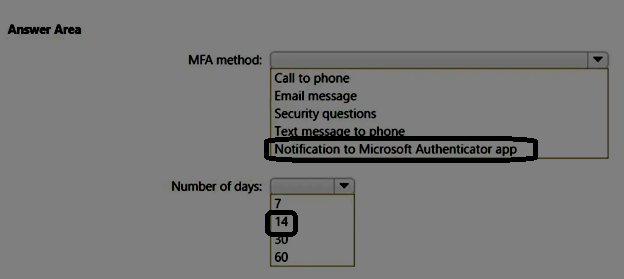
Correct Answer:
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains the objects shown in the following table.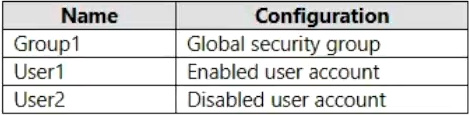
You configure Azure AD Connect to sync contoso.com to Azure AD.
Which objects will sync to Azure AD?
Correct Answer:
D
🗳️
You have a Microsoft 365 E5 subscription.
You need to create Conditional Access policies to meet the following requirements:
All users must use multi-factor authentication (MFA) when they sign in from outside the corporate network.
Users must only be able to sign in from outside the corporate network if the sign-in originates from a compliant device.
All users must be blocked from signing in from outside the United States and Canada.
Only users in the R&D department must be blocked from signing in from both Android and iOS devices.
Only users in the finance department must be able to sign in to an Azure AD enterprise application named App1. All other users must be blocked from signing in to App1.
What is the minimum number of Conditional Access policies you should create?
Correct Answer:
B
🗳️