

You have a Microsoft 365 E5 subscription.
You create a data loss prevention (DLP) policy named DLP1.
You need to ensure that endpoint rule actions are available in the advanced DLP rules for DLP1.
To which location should you apply DLP1?
Correct Answer:
D
🗳️
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint.
All the devices in your organization are onboarded to Microsoft Defender for Endpoint.
You need to ensure that an alert is generated if malicious activity was detected on a device during the last 24 hours.
What should you do?
Correct Answer:
D
🗳️
You have a Microsoft 365 E5 subscription that contains a domain named contoso.com.
You deploy a new Microsoft Defender for Office 365 anti-phishing policy named Policy1 that has user impersonation protection enabled for a user named user1@contoso.com.
You discover that Policy1 blocks email messages from a regular contact named user1@fabnkam.com.
You need to ensure that the messages are delivered successfully.
What should you do for Policy1?
Correct Answer:
D
🗳️
HOTSPOT
-
You have a Microsoft 365 E5 subscription.
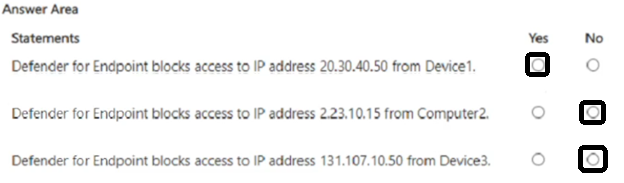
You have devices onboarded to Microsoft Defender for Endpoint as shown in the following table.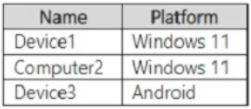
You create the device groups shown in the following table.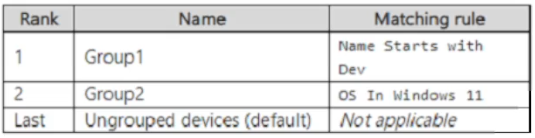
IP address indicators are defined as shown in the following table.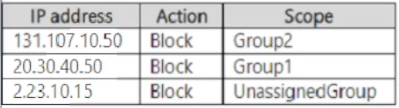
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.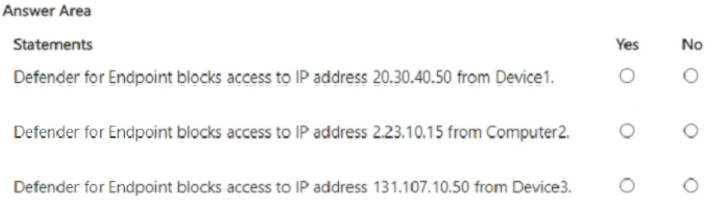
Correct Answer:
Your company has a Microsoft Entra tenant named contoso.com and a Microsoft 365 subscription.
All users use Windows 10 devices to access Microsoft Office 365 apps.
All the devices are in a workgroup.
You plan to implement password less sign-in to contoso.com.
You need to recommend changes to the infrastructure for the planned implementation.
What should you include in the recommendation?
Correct Answer:
A
🗳️
You have a Microsoft 365 E5 subscription.
You plan to implement an authentication policy that will user FIDO2 security key as a user authentication method.
You need to ensure that during enrollment, each FIDO2 security key is verified by using the FIDO Alliance Metadata Service.
Which setting should you enable?
Correct Answer:
C
🗳️
HOTSPOT
-
You have a Microsoft 365 E5 subscription.
You are investigating a suspicious email message that generated alerts in the Microsoft Defender portal.
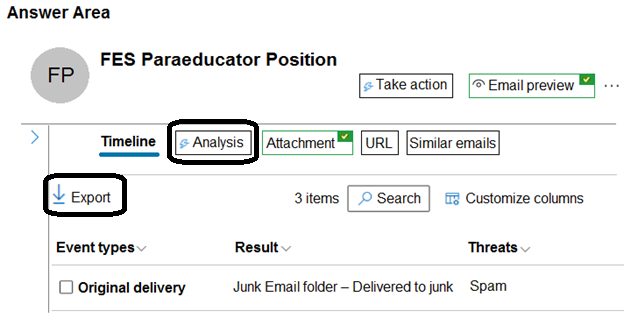
You need to examine the email message header and submit the message to Microsoft for review.
Which two settings should you use? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.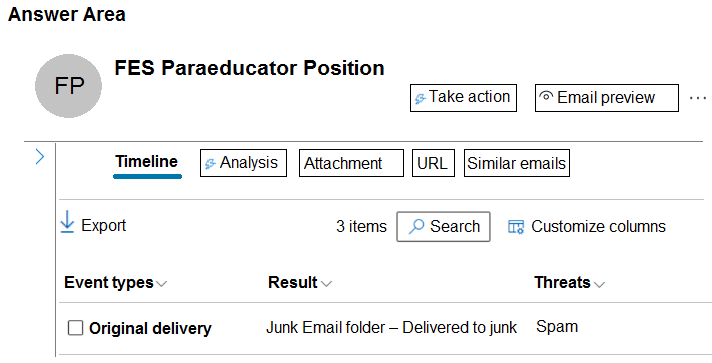
Correct Answer:
You have a Microsoft 365 E5 subscription.
You create the users shown in the following table.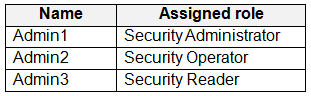
You plan to use Microsoft Entra ID Protection.
Which users will be added automatically to the User at risk detected alerts list?
Correct Answer:
D
🗳️
HOTSPOT
-
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.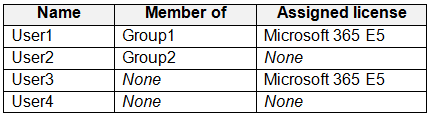
The subscription contains the groups shown in the following table.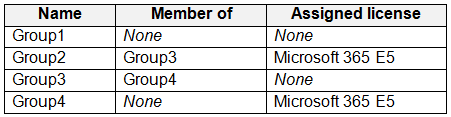
Which users and groups can you delete? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.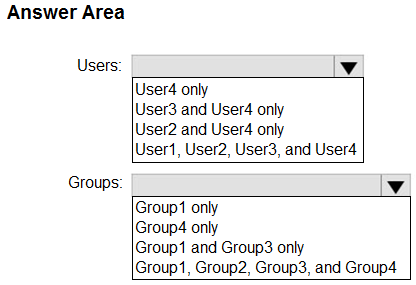
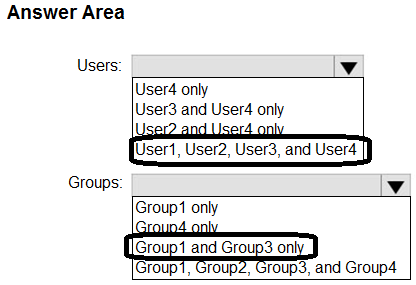
Correct Answer:
You have a Microsoft 365 E5 subscription.
You create a user named Admin1.
You need to ensure that Admin1 can view Endpoint security policies from the Microsoft Defender portal. The solution must follow the principle of least privilege.
Which Microsoft Entra role should you assign to Admin1?
Correct Answer:
B
🗳️